A Guide for Data-Driven Marketing: How to use Predictive Analytics Models to Drive Business Growth
Learn how marketers can use predictive models, like classification, clustering, regression, and time series, to power social listening, forecast trends, and drive data-backed decisions with custom pipelines from Datastreamer.
A Guide to Building Custom Data Pipelines with Datastreamer
Learn how to build custom data pipelines with Datastreamer to ingest, classify, and analyze data—empowering your team to scale operations, uncover insights, and make data-driven decisions with confidence.
How To Build Threat Detection Pipelines Using Datastreamer
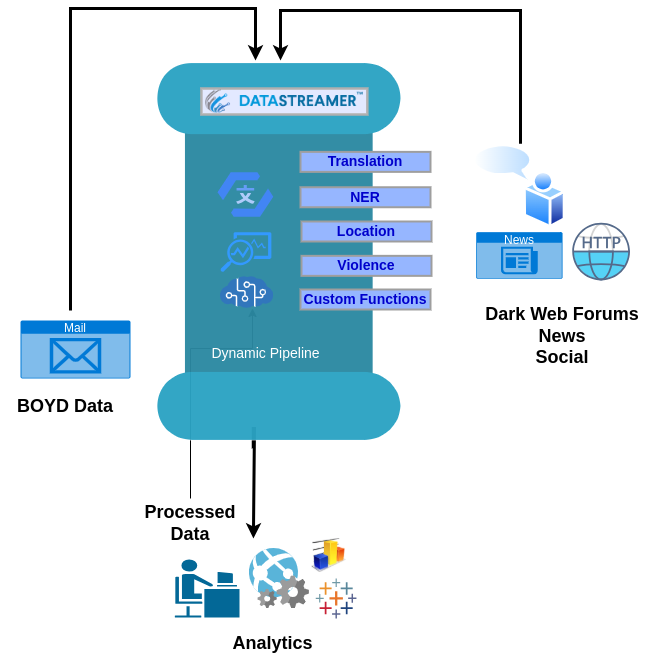
Learn how to build a proactive threat detection pipeline using Datastreamer. This guide shows how to ingest, normalize, and enrich data from sources like social media, news, and dark web forums. It also covers translation, entity recognition, sentiment analysis, and violence classification to help teams gain real-time threat intelligence and stay ahead of emerging risks.
A Guide to Data Pipeline Design: Low-Latency or High-Throughput

Compare low-latency and high-throughput data pipelines, explore component strategies, and learn how to build hybrid architectures that balance speed and scale with Datastreamer.
